Overview
Multi-Factor Authentication (MFA) is an authentication method that grants users access to your SmartSimple Cloud system only after they have successfully provided two or more forms of evidence to an authentication mechanism.
The security benefits of MFA are significant; while a user may lose their authentication device or be deceived into disclosing a password, the likelihood of both events occurring simultaneously is greatly diminished. Consequently, implementing MFA enhances an organization's security by necessitating that users verify their identity with more than just their login credentials.
SmartSimple Cloud offers two methods for implementing MFA:
- Time-based One-Time Password (TOTP) utilized through an authenticator application, which is more secure and appropriate for users with elevated access, such as global administrators or internal staff.
- Single Use Verification Code sent via email or SMS, which is more suitable for external users or those who log in infrequently.
Note: As of the March 2023 upgrade, MFA and password reset emails are dispatched from non-production environments. Should you wish to impose role restrictions for access to your backup environment, the relevant setting can be found at Menu icon > Global Settings > Security tab > System Feature Permissions > Feature tab > Restrict Login to Backup Environment to these Roles. When testing MFA and password reset emails in non-production environments, it is advisable to utilize a test user and test email.
Configuration
To enable multi-factor authentication, please follow the steps outlined below:
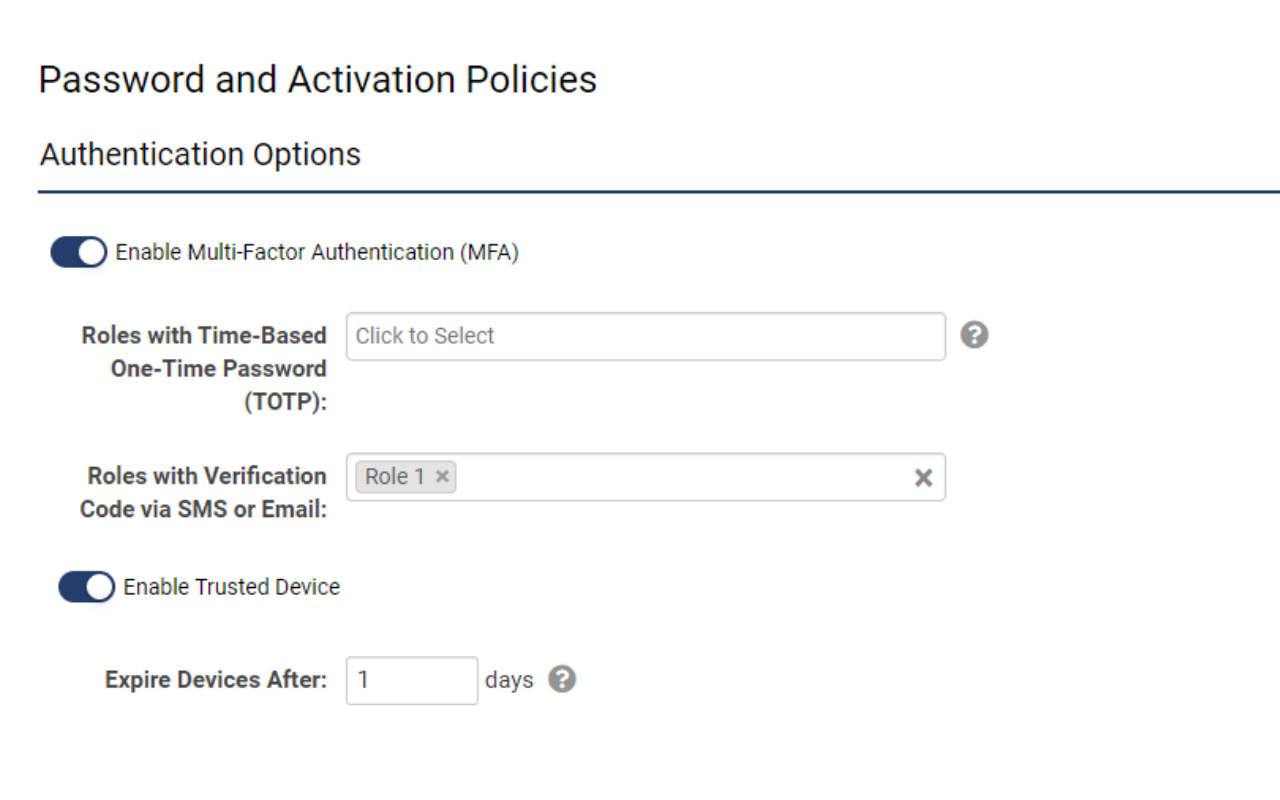
- Navigate to Global Settings > Security > Password and Activation Policies
- Scroll to Authentication Options and activate Enable Multi-Factor Authentication
- Specify the roles that necessitate authentication via TOTP and/or Verification Code. If a role is assigned to both methods, only TOTP will be utilized.
NOTE: Selecting the Everyone option means that this setting does not require updates when new roles are created.
Time-Based One-Time Password (TOTP) Implementation
A time-based one-time password can be generated using an authentication device (such as a mobile phone) to provide an additional security layer for authenticating logins.
Configuring TOTP Multi-Factor Authentication for Specific Roles
- In your SmartSimple instance (logged in as Global Admin), navigate to Menu Icon > Global Settings.
- Proceed to the Security tab > Password and Activation Policies > Under “Authentication Options,” activate Enable Multi-Factor Authentication (MFA).
- In the setting labeled Roles with Time-Based One-Time Password (TOTP), identify the roles for which you wish to enable multi-factor authentication.
- Activate Enable Trusted Device if you would like users to be able to bypass entering a code for a specified period after the code has been successfully entered. If enabled, please also specify the duration until the authentication bypass expires.
- Scroll to the bottom of the page and click Save.
Logging in for the First Time with TOTP
To utilize TOTP effectively, users must first download an authenticator application onto their mobile devices. Popular authentication applications include Google Authenticator, Microsoft Authenticator, or 2FAS. Upon logging into the system for the first time after TOTP has been activated for the user's role, the user must adhere to the following steps:
- If TOTP is enabled on their account, users will encounter the following screen during their next login:
- Follow the instructions displayed on the screen. Begin by installing an authenticator application on your mobile device.
- On your mobile device, open the authenticator application and select the option to add a new device or scan a QR code. Each application may have different procedures.
- The application may prompt you for a QR code or a secret key. On your SmartSimple MFA setup page, click the button labeled Show TOTP Key and QR Code. This action will reveal the QR code and secret key used with the authentication application.
- Utilize the mobile application to scan the QR code or manually input the secret key into the application. Upon completion, a new device will be added to your list within the application.
- The mobile application will generate a time-based verification code. Enter this code into the field labeled Enter Verification Code on the setup page.
- Click Submit.
Procedure for Resetting TOTP When the Mobile Device is Misplaced
NOTE: In the event that a mobile device associated with TOTP is misplaced, the TOTP must be reset by a Global Administrator or by an individual in a role with the authorization to reset TOTP for other user roles.
Should a user's device be misplaced, the following steps will enable an internal user in the aforementioned roles to reset the user's TOTP:
- Access the profile of the user who requires the TOTP credentials to be reset.
- From the Actions dropdown menu, select Edit Roles and Access.
- In the subsequent modal window, select the button labeled Reset TOTP.
- The user may now log in as usual, following the prompts on the subsequent Set Up Multi-Factor Authentication screen.
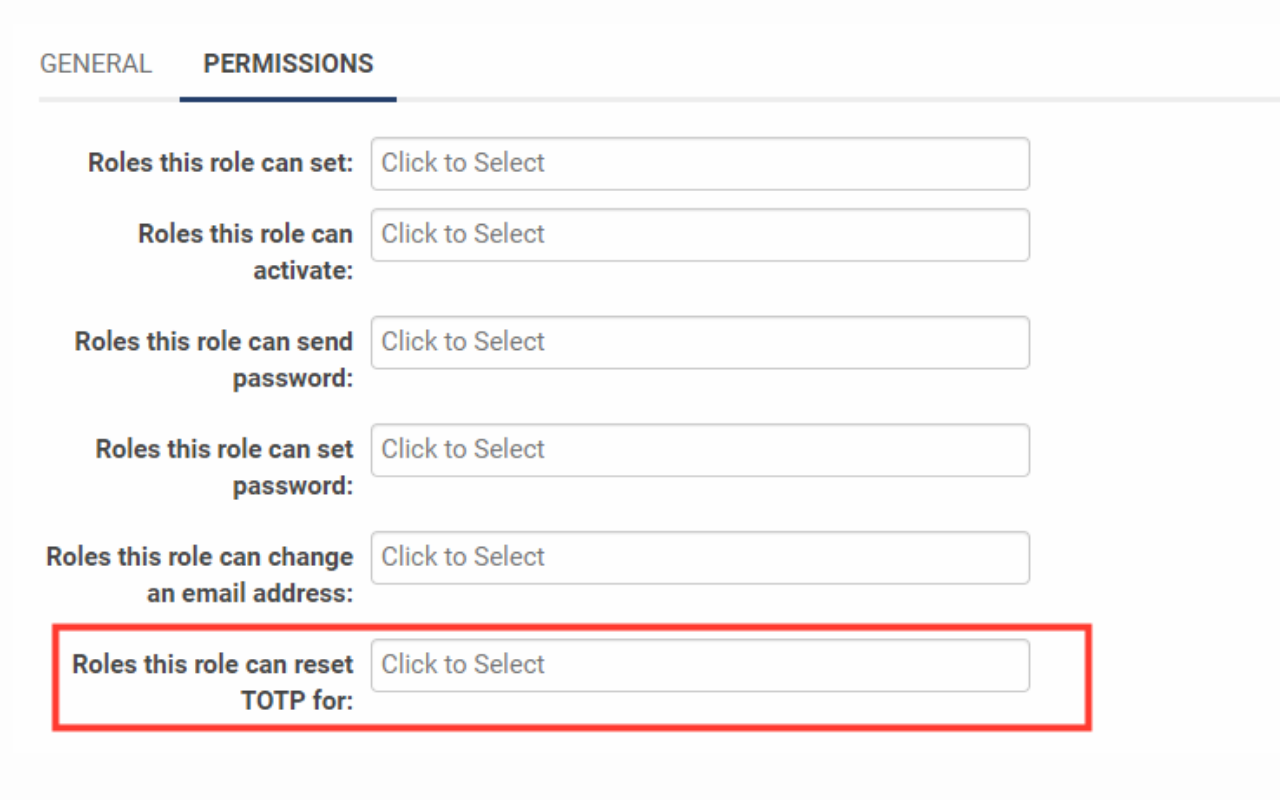
Identifying Roles Authorized to Reset TOTP
- In your SmartSimple instance (logged in as a Global Administrator), navigate to the Main Menu and select Global Settings.
- Proceed to the Users tab and click on Roles.
- Edit the role that you wish to authorize for resetting TOTP on behalf of other users. For optimal security practices, this role should be restricted to internal use only.
- Select the Permissions tab.
- In the field labeled Roles this role can reset TOTP for, select the other roles for which this role can reset TOTP.
Note: In addition to the selected roles, you must also possess permissions to activate users (Roles this role can activate setting) as this is part of the activation procedure.
- Click Save.
Implementation of Single-Use Verification Codes
A single-use verification code is a uniquely generated number sent to the user via email or SMS. As verification codes typically expire within a few minutes, users will be prompted for their single-use code each time they log into the system.
Configuring Verification Codes for Email
Note: If you are utilizing the SMTP Relay with an IP restriction for sending emails, ensure that the IP addresses of your environments (backup, testing, production) are included in your IP list. Should you require assistance in identifying the IPs of your environments or have any inquiries, please contact our support team.
The most straightforward method for establishing MFA is through the email address used for user registration and login.
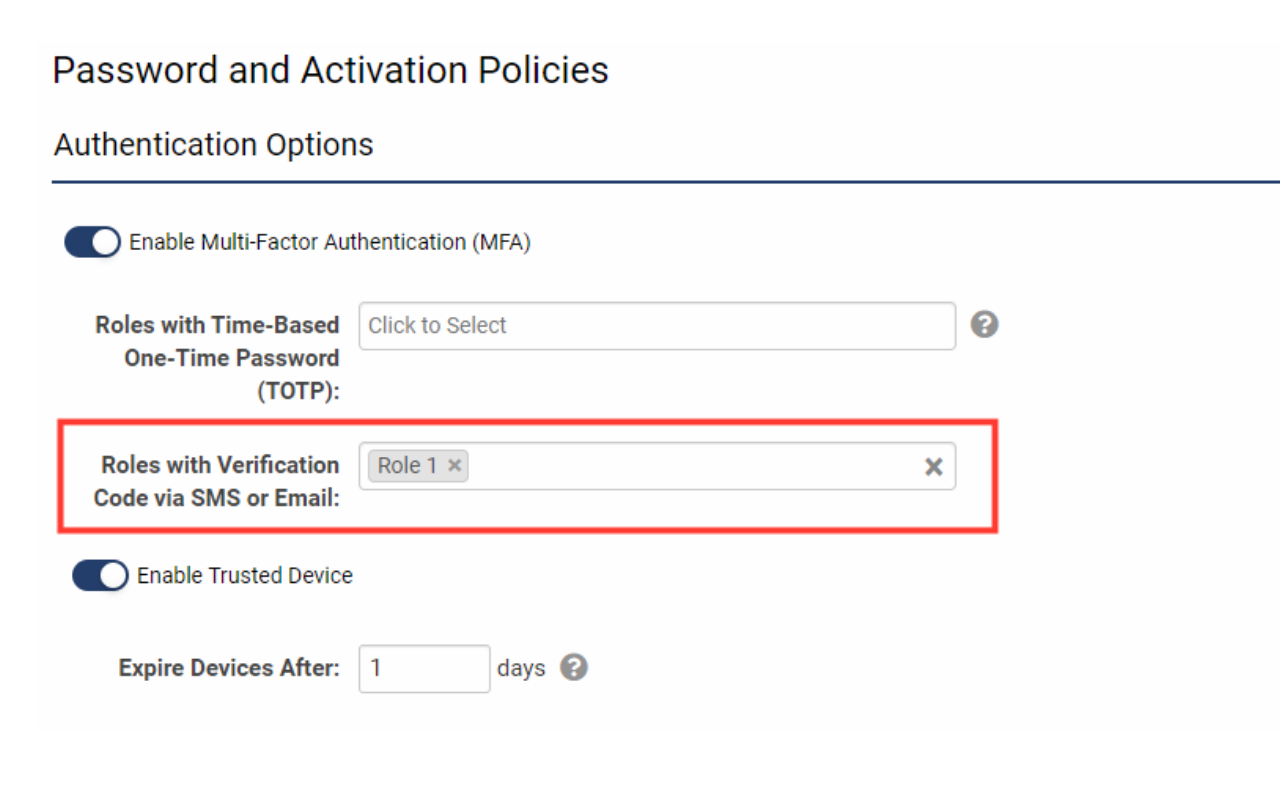
- Navigate to Menu Icon > Global Settings > Security tab > Password and Activation Policies and then scroll down to the section labeled Authentication Options.
- Enable Multi-Factor Authentication. Additional settings for various authentication methods will be displayed.
- Under the Roles with Verification Code via SMS or Email setting, determine which roles require authentication through a verification code sent to the email address used for login. Click the Save button at the bottom of the page to implement the changes.
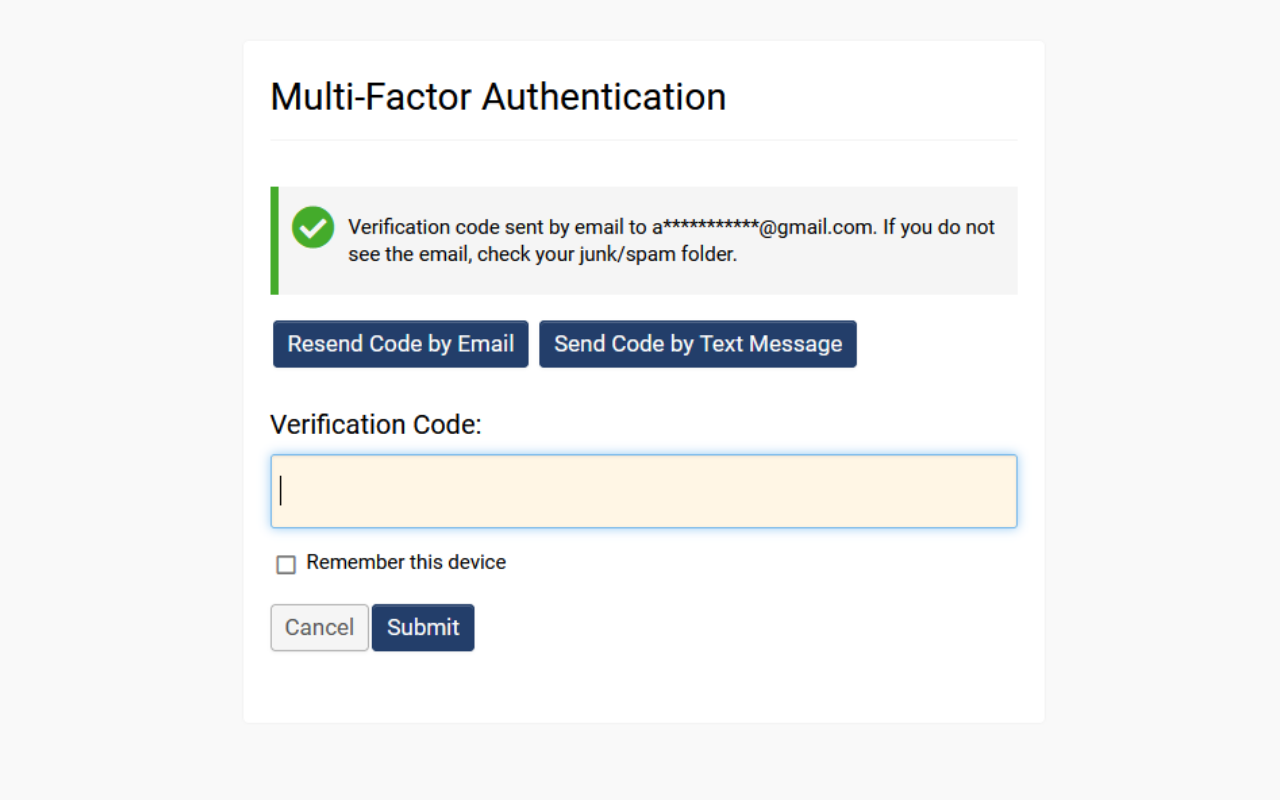
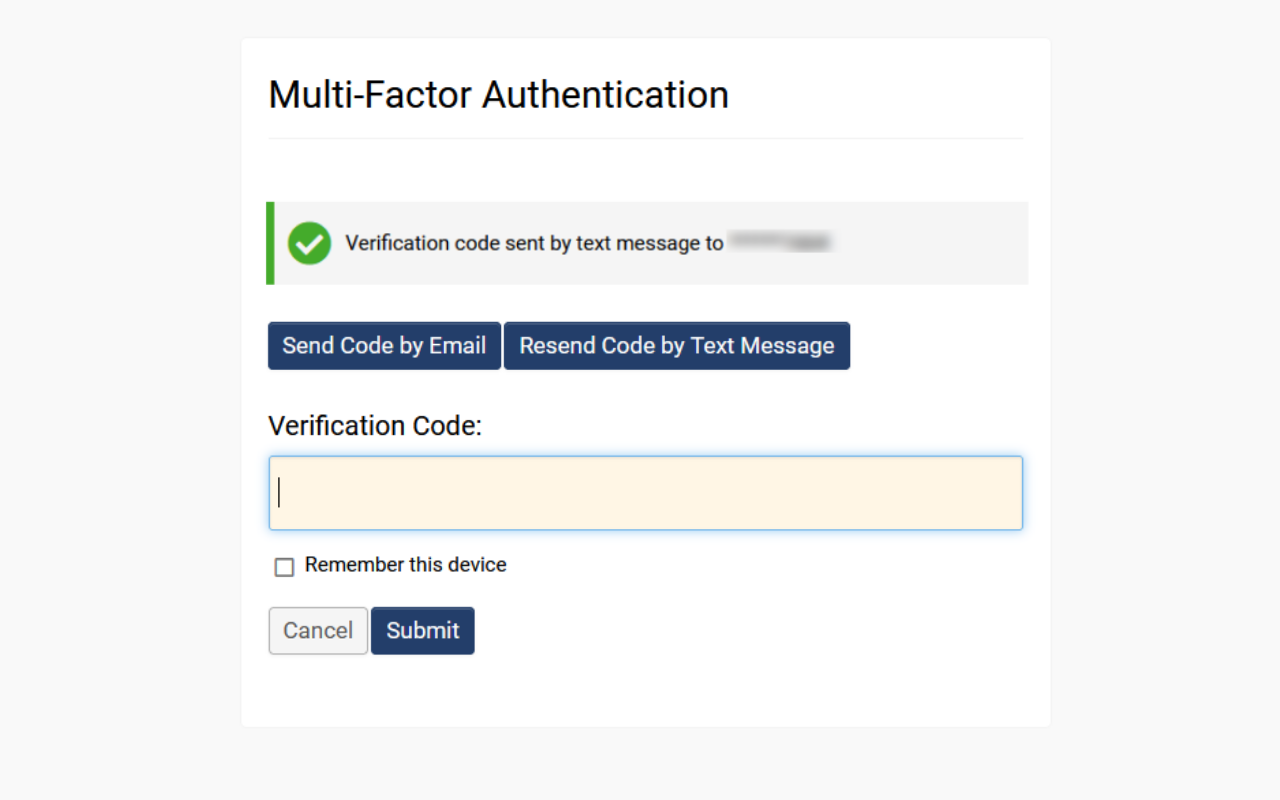
Logging in with a Verification Code Sent via Email
When a user has been assigned a role that necessitates a verification code, they may log in by following these steps:
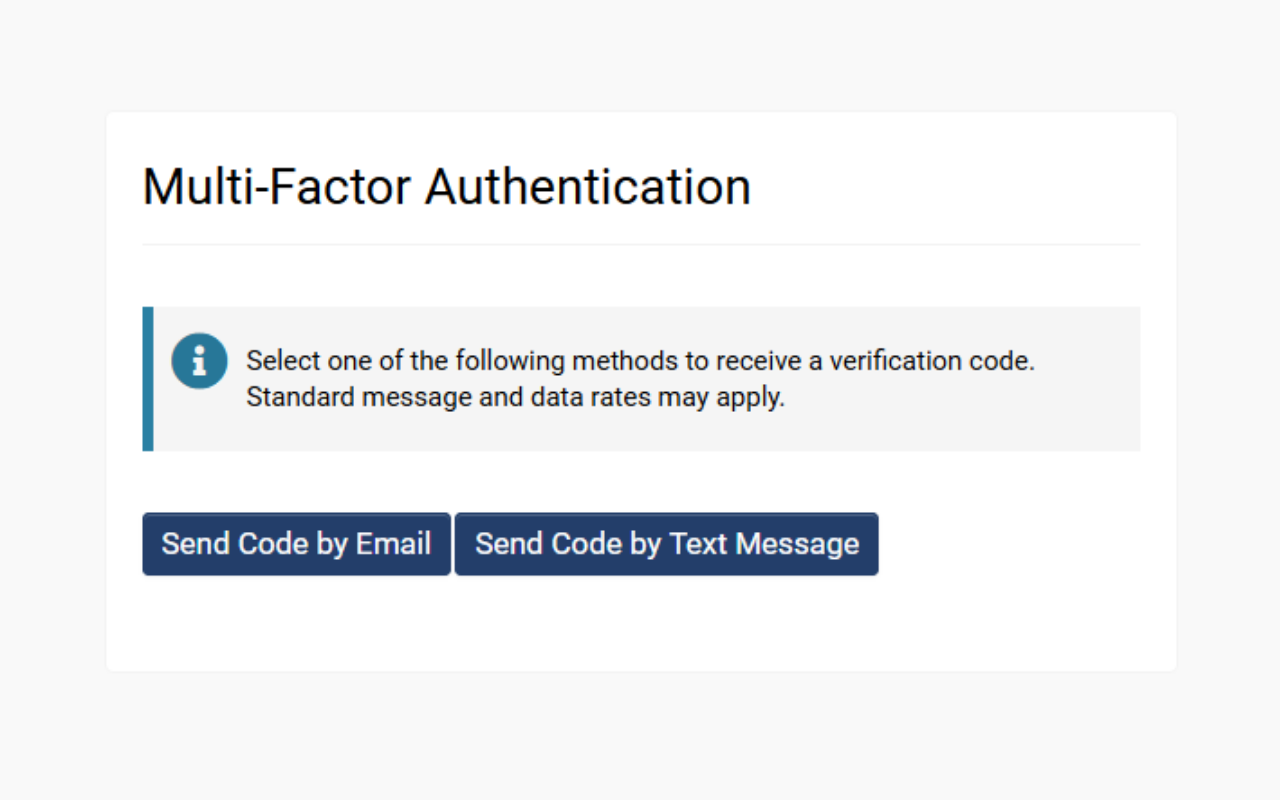
- Upon logging in with their email and password, the user will be directed to a page where they can click a button labeled Send Code by Email.
- They will be prompted to enter the verification code that was sent to their email.
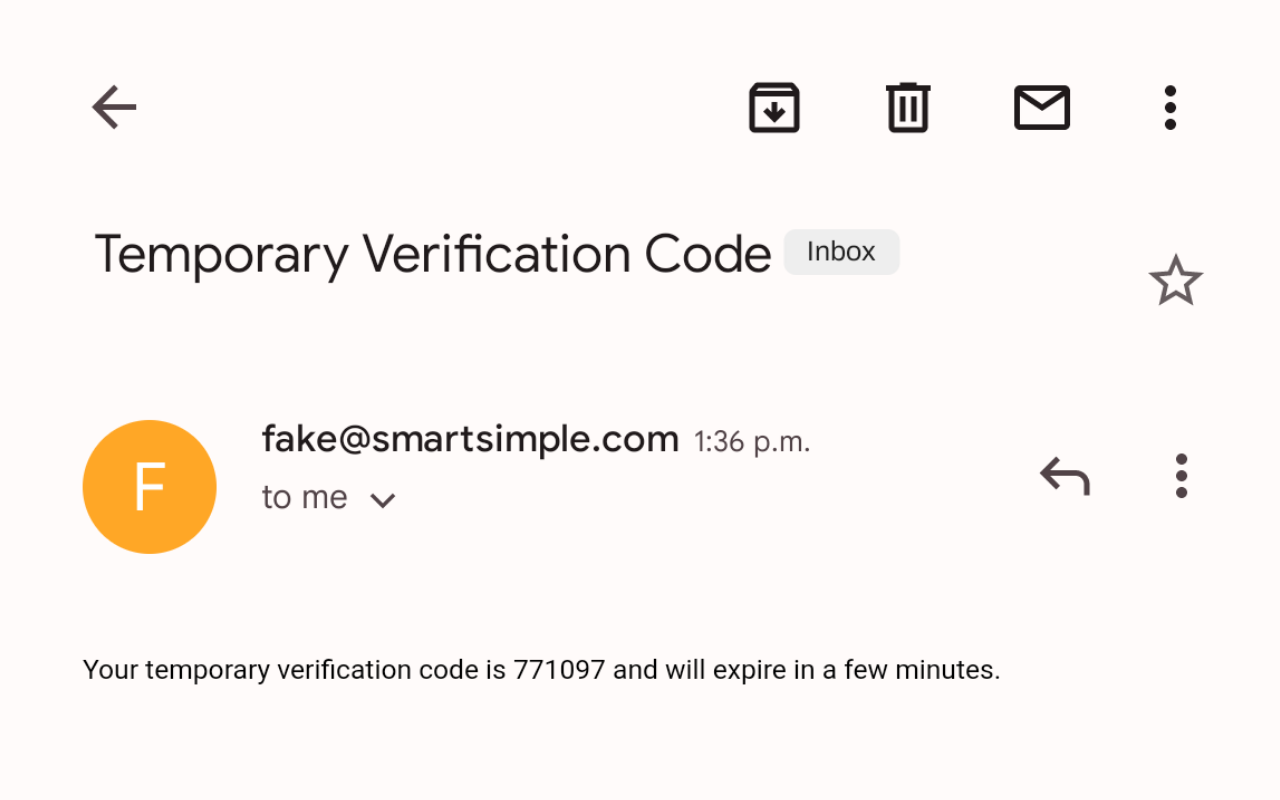
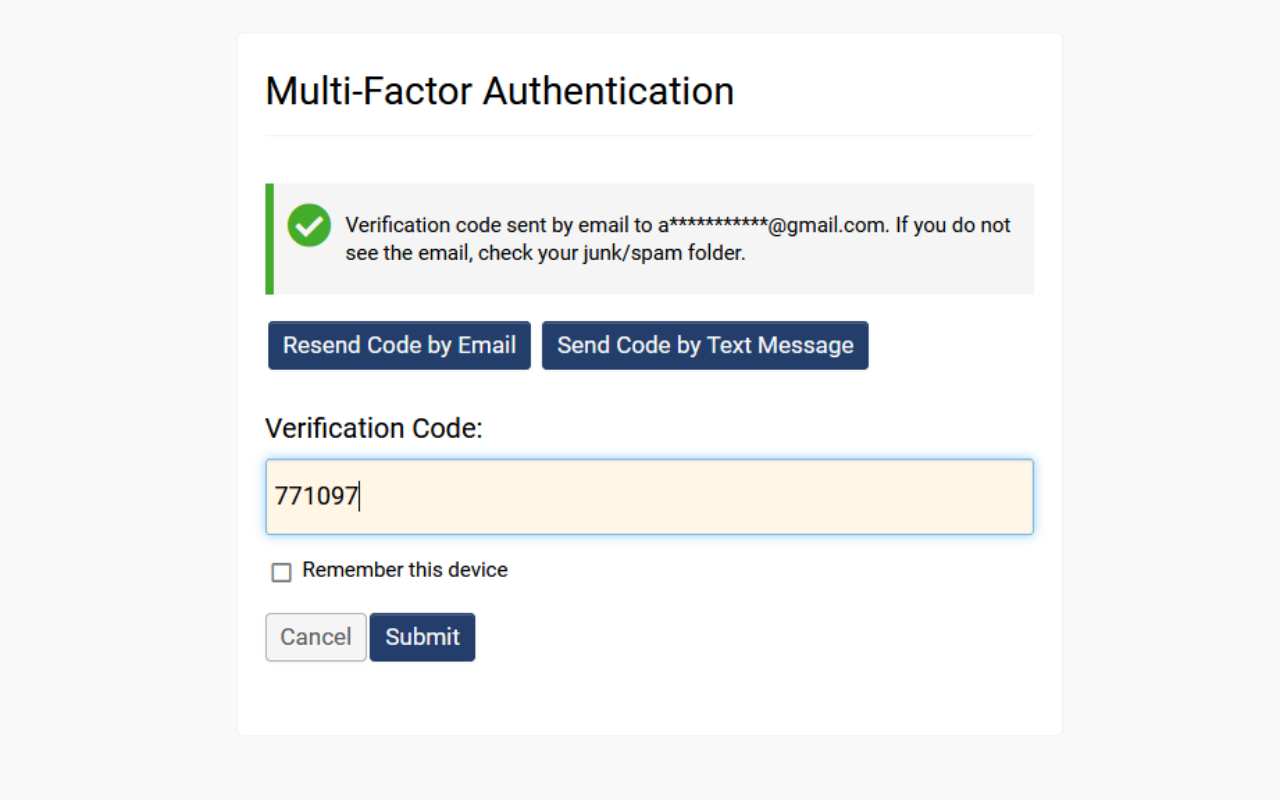
- The user must access their email to retrieve the verification code.
- Input the verification code into the designated field and then click Submit to complete the authentication process and log into the system.
Configuring Verification Codes for SMS
Bring Your Own SMS Provider License
Clients have the option to establish their own Vonage account for the purpose of sending SMS messages from their system. For further information, please visit the Vonage website to review their SMS API. After setting up your account, please navigate to Global Settings > Integrations tab > Integration Key Management > Create an integration key, ensuring that the Type is designated as "Vonage." You will be required to input your Vonage API Key, API Secret, and either a North American or International virtual number.
Note: SmartSimple representatives must enable the SMS feature within your system.
Logging in with Verification Codes via SMS
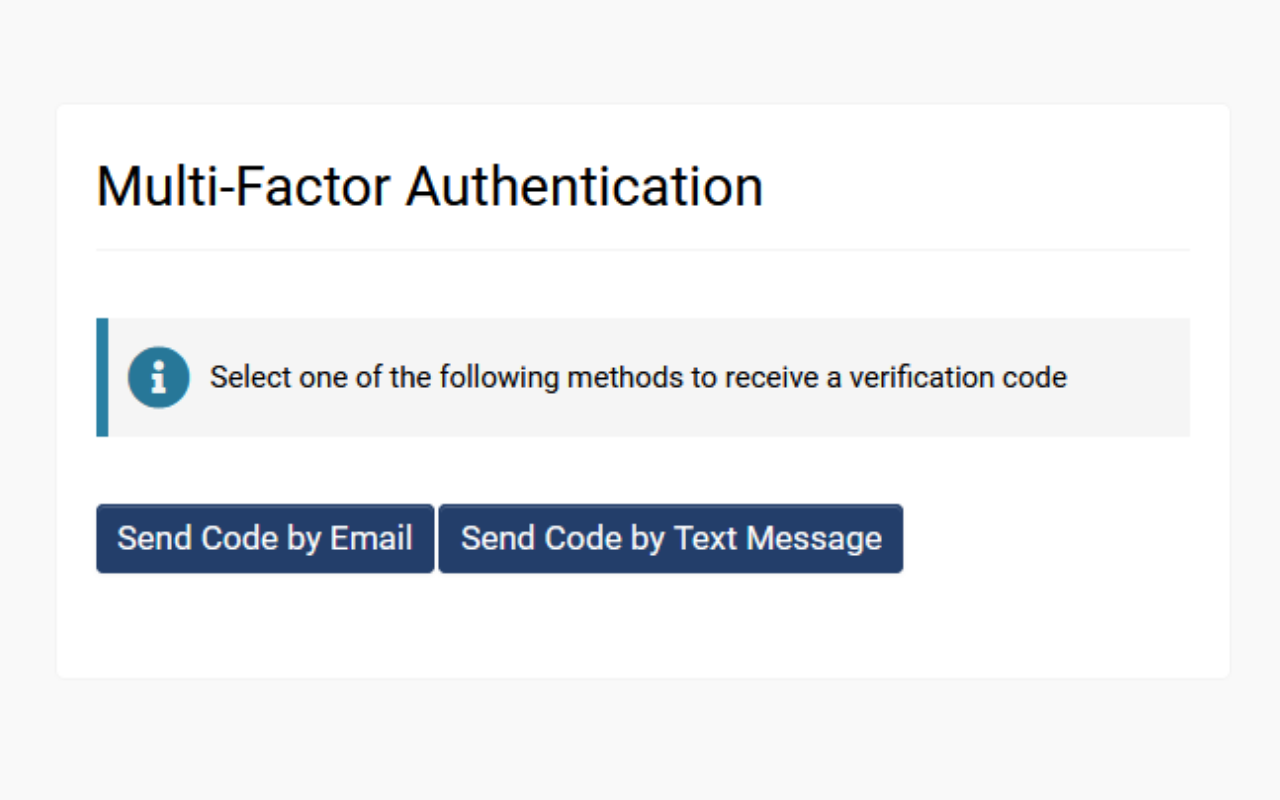
- Upon logging in, users will be presented with the option to receive a verification code via email or SMS. The user may select Send Code by Text Message.
- The user can then check their mobile messages, input the code into the designated field, and click Submit to complete the authentication process and log into the system.
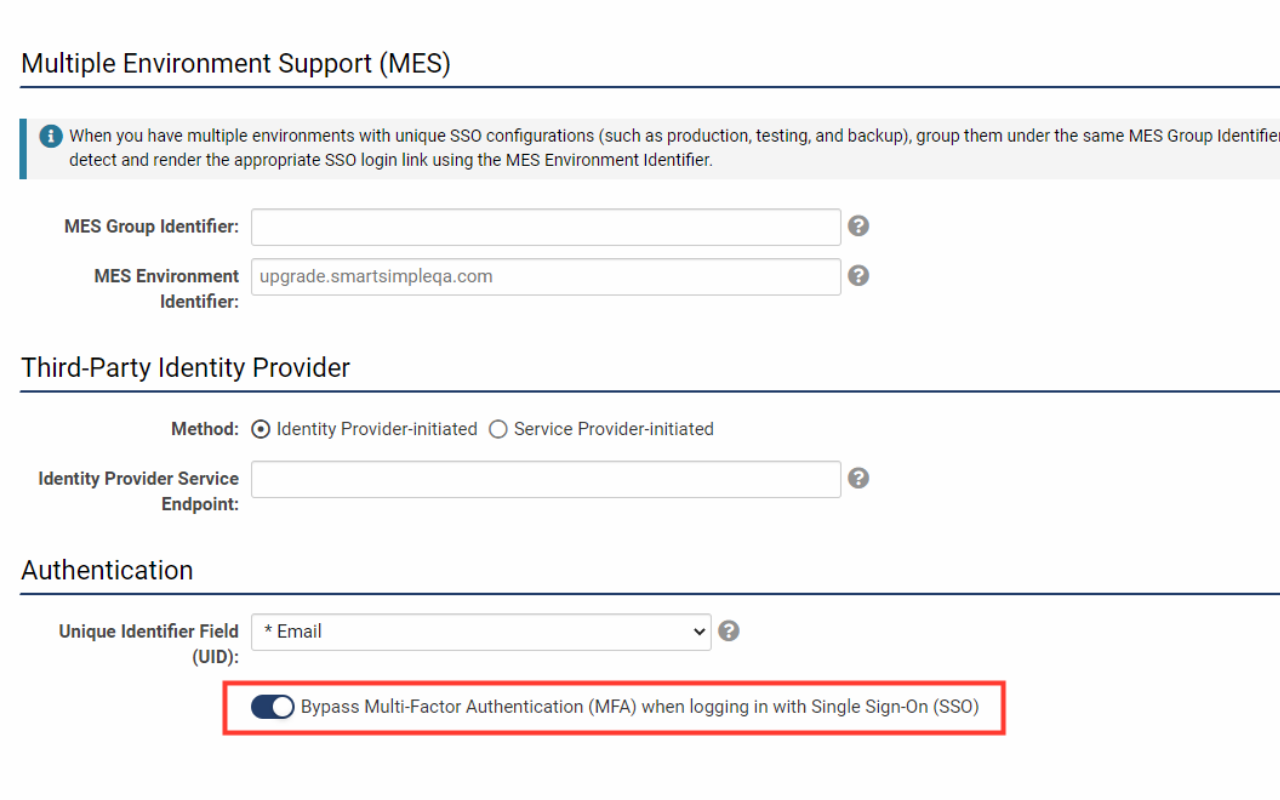
Bypassing Multi-Factor Authentication for Single Sign-On
If multi-factor authentication is enabled, it may be bypassed for users logging in via single sign-on (SSO). To bypass MFA, navigate to Global Settings > Integrations tab > Single Sign-On > Edit an SSO setting > Activate Bypass Multi-Factor Authentication (MFA) when logging in with Single Sign-On (SSO).
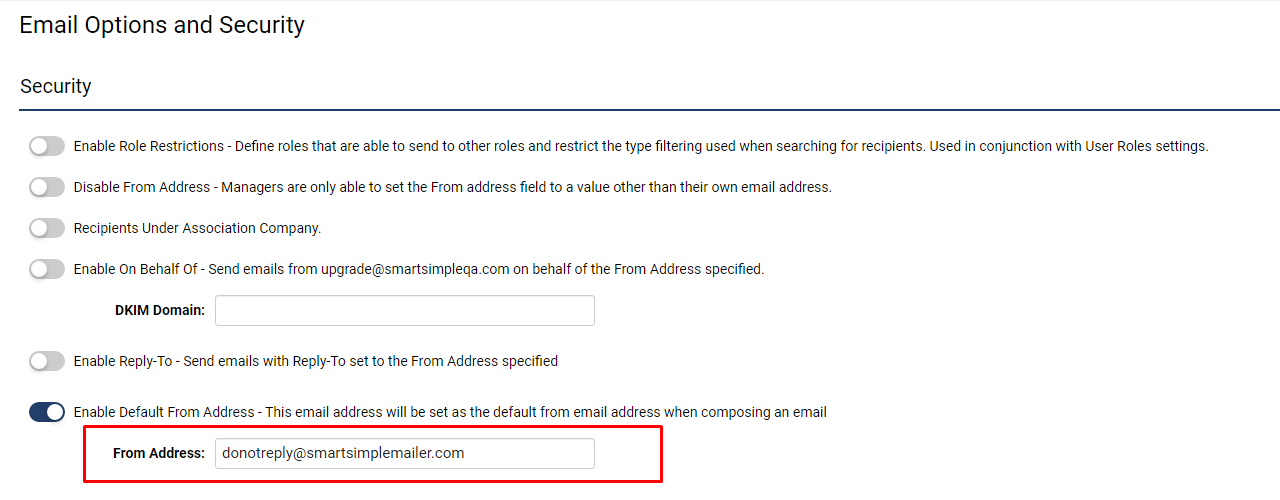
Setting up a Default Email Address
If you are utilizing SMTP relay and/or possess a dedicated instance (your own domain), it is imperative to establish a default email address that aligns with your domain. Otherwise, your default email address should be set to donotreply@smartsimplemailer.com (US), or donotreply@smartsimplemailer.eu (Europe), or donotreply@smartsimplemailer.ca (Canada). To set up a default email address, please follow these steps:
- Access the Menu icon > Global Settings > Communications tab.
- Select Email Options and Security.
- Activate Enable Default From Address.
- Input your preferred From Address.
- Click Save.
Settings Explained
| Setting | Description |
| Enable Multi-Factor Authentication | Activates MFA for the entire instance; however, it will not take effect unless user roles are specified. |
| Roles with Time-based One-time Password (TOTP) | Links one or more roles with authentication verified through an authenticator application such as Google or Microsoft Authenticator. |
| Roles with Verification Code via SMS or Email | Links one or more roles with authentication verified through either email or SMS. The user may select at the point of verification to receive an email containing the one-time code or an SMS message containing the one-time code. SMS must be enabled by SmartSimple and will incur additional costs. Please consult Support or your account manager for further details. |
| Enable Trusted Device | This option allows for the bypassing of MFA authentication for specific roles on designated devices. |
| Trusted Device Expiry | Determines the frequency of the MFA prompt, based on the specified number of days. If set to one, the user will be prompted daily for an MFA verification code. If set to five, the user will be prompted every five days. |